
M365 Best Practices White Paper
A Microsoft 365 Security Guide with Best Practices for ITprofessionals and the community Key takeaways from this White paper: GET THE WHITE PAPER: https://comptecit.com/Microsoft-365-Security-Guide-Whitepaper.pdf

A Microsoft 365 Security Guide with Best Practices for ITprofessionals and the community Key takeaways from this White paper: GET THE WHITE PAPER: https://comptecit.com/Microsoft-365-Security-Guide-Whitepaper.pdf

🎉We’re thrilled to announce that COMPTEC I.T has achieved a Veeam Silver Partner status! 🙌This partnership allows us to deliver exceptional data protection and cloud solutions

🎬Whether you are a small business owner or an IT professional, understanding your obligations under the NIS2 Directive is critical. In this video (🇬🇷 Greek

From COMPTEC IT Team, warm wishes for a Happy Easter to you and your loved ones! ✨

A newly disclosed remote code execution (RCE) vulnerability in Veeam Backup & Replication (🔥CVSS 9.9) enables authenticated domain users to execute arbitrary code on affected

SMB over QUIC is a relatively new, promising file-sharing technology that, given the advancement of cloud deployments, remote work, and zero-trust architectures, has a good

From all of us at COMPTEC IT, we wish you a Merry Christmas and a prosperous New Year!

We are happy to share that Konstantinos Xanthopoulos obtained a new certification: Certified Payment Security Practitioner (CPSP v2.0) from Network Intelligence!

💻 Black Friday is here with discounts reaching up to 70% on selected products: 🔔 Don’t miss the chance to upgrade your equipment at the

🎉 Congratulations to Konstantinos Xanthopoulos, CISSP!We’re proud to share that he has achieved the CISSP certification! 👏

We are committed to informing you about important technology developments that may impact your business. We have important information to share regarding the end-of-support dates

https://www.linkedin.com/embed/feed/update/urn:li:share:7255358135266144257

In today’s digital world, passwords are crucial in securing access to sensitive information. However, with the increasing number of online accounts and the complexity of

Unlocking the Power of Service Delivery Today’s landscape requires a rapid pace, automating what could be automated but also a solid and robust foundation and
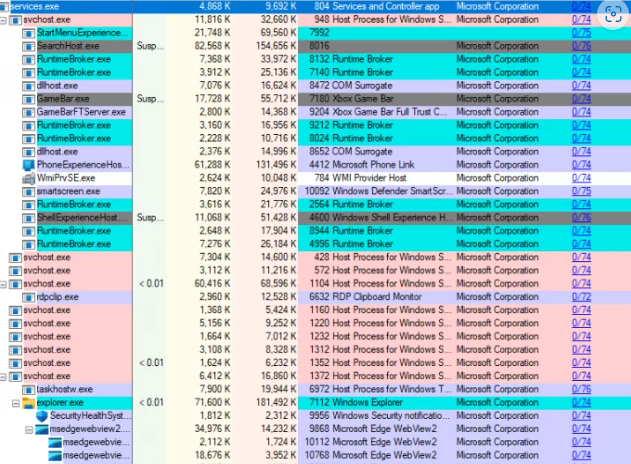
Sysinternals Process Explorer is a powerful tool for I.T professionals to monitor and manage system processes, security, and performance. The software, free to download from
