What is MFA Fatigue & how to defend against it

What is an MFA Fatigue Attack?
An MFA Fatigue attack is a strategy used by threat actors to abuse sign-in security by forcing users to grant them access to get relief from the MFA flood.
The method is also known as MFA bombing and is considered a high-profile attack.
How it works
This strategy, combined with several other Social Engineering techniques, can be very effective. Consider the following imaginary (yet occurring every day) scenario:
The attacker spots a person who holds a role in an organisation’s Accounting department and ensures to get as much information as possible about that individual.
Let’s call our fictional organisation XYZ and the attacked person Mary.
Presumably, the malicious actor somehow manages to obtain Mary’s password; this could result from Social Engineering or any other attacking vector.
At that point, the attacker should already have enough information to consider their chances of having the individual’s account compromised.

The attacker then picks a date and time when they believe Mary would be less vigilant such as a busy day late afternoon, and starts bombarding her with a massive number of authentication attempts.
Due to human nature, there are some strong chances that Mary, desperate to stop receiving this notification storm, ultimately chooses to approve a request.
And that is it. That is all it takes for a malicious actor to bypass the MFA security measure and get access to XYZ’s sensitive information.
How to deal with it
To defend against this high-profile threat, you must configure the MFA number verification and geographic location features available to your tenant:
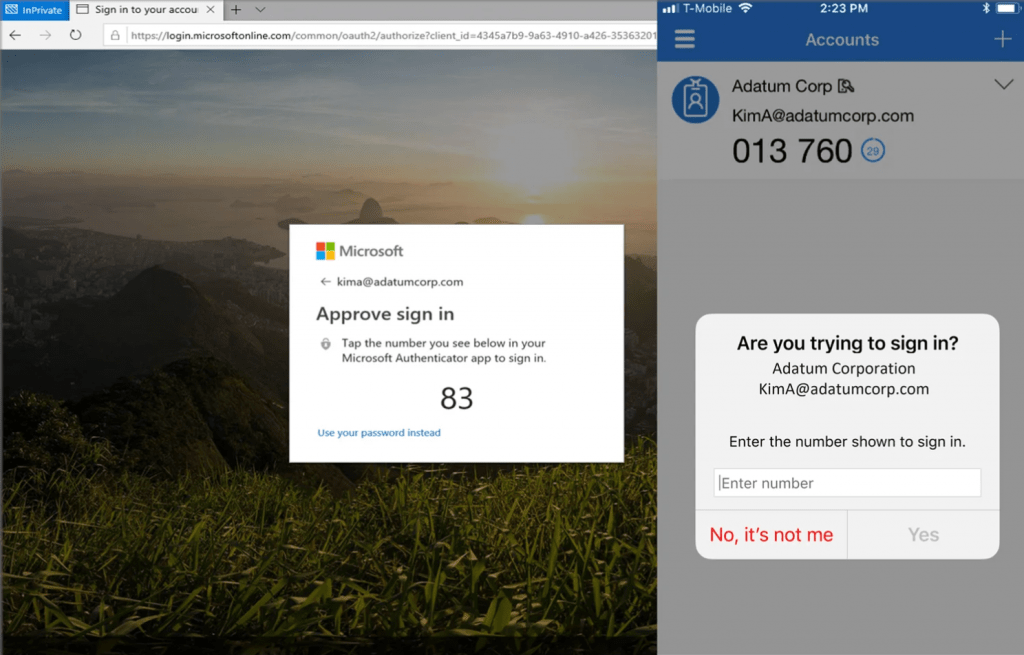
Isn’t the request now looking more suspicious than it was before?
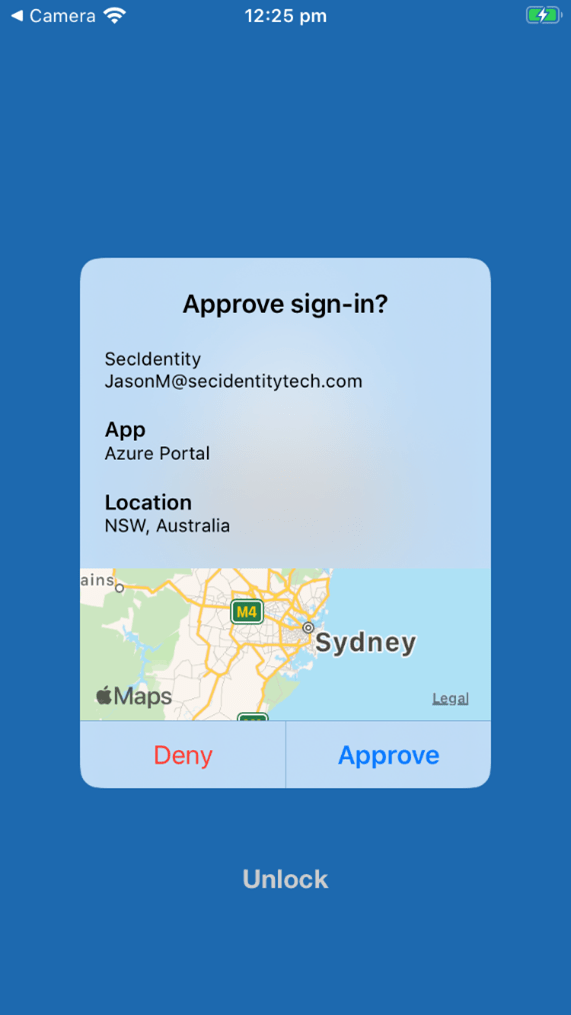
Microsoft plans to enable it by default for all Azure Active Directory tenants soon, but until then, why not give it a shot (or call us to set it up for you)?
If you found this informative, don’t miss out on downloading our Security Guide with tips and tricks for Microsoft 365:


