We are happy to share that Konstantinos Xanthopoulos obtained a new certification: Certified Payment Security Practitioner (CPSP v2.0) from Network Intelligence!
🎉 Congratulations to Konstantinos Xanthopoulos, CISSP!We’re proud to share that he has achieved the CISSP certification! 👏
We are committed to informing you about important technology developments that may impact your business. We have important information to share regarding the end-of-support dates for various versions of Windows 10 and Windows 11. For an OS, this means no further security updates, which puts our data at risk. Presently, the following Windows versions are approaching or have already reached their end […]
https://www.linkedin.com/embed/feed/update/urn:li:share:7255358135266144257
In today’s digital world, passwords are crucial in securing access to sensitive information. However, with the increasing number of online accounts and the complexity of password requirements, remembering, sharing and managing passwords poses a significant challenge for businesses. This is where Password Management software jumps in. The why’s Password Management software is a tool designed […]
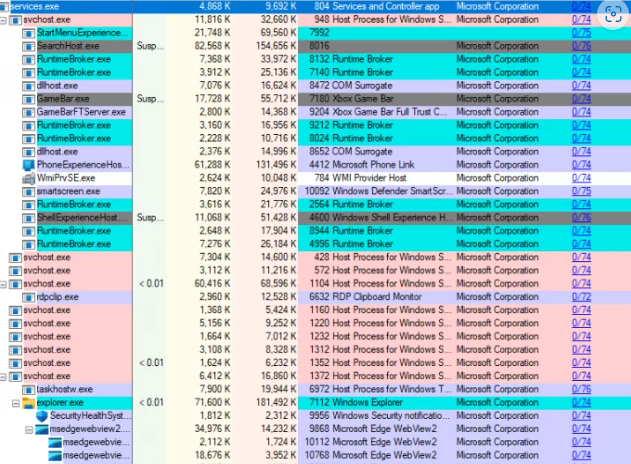
Sysinternals Process Explorer is a powerful tool for I.T professionals to monitor and manage system processes, security, and performance. The software, free to download from the Sysinternals website, was originally released in 1996 by Mark Russinovich and Bryce Cogswell and has since evolved to offer a comprehensive set of features for process management and system […]
Many small businesses make the mistake of skipping policies. They feel that things don’t need to be so formal. They’ll just tell staff what’s expected when it comes up and think that’s good enough. But this way of thinking can cause issues for small and mid-sized business owners. Employees aren’t mind readers. Things that you […]
🔍 What’s Happening? ⚠ Attackers overwhelm users with spam emails, primarily newsletter sign-up confirmations from legitimate organisations.⚠ Follow-up phone calls from individuals impersonating IT team members offer assistance and prompt users to download remote monitoring software like AnyDesk or use Microsoft’s Quick Assist feature.⚠ The goal is to establish a remote connection, allowing attackers to […]
💡 Our infographic highlights the key changes coming to Windows Server 2025, including new features and the removal of outdated functionalities. Here’s a quick rundown of what you need to know: New features:✅ A new functional level for forests and domains.✅ Delegated Managed Service Accounts (dMSA) with improved security.✅ Support for TLS 1.3 for LDAP […]
In an era where digital transformation is not just an option but a necessity, Microsoft 365 has emerged as the cornerstone of corporate productivity, enabling seamless communication, collaboration, and information management worldwide. However, the reliance on Microsoft 365 also introduces significant security vulnerabilities that can be exploited by cyber adversaries, making security vulnerability management an […]
📢 #NIST Releases Version 2.0 of Landmark Cybersecurity Framework. This is the first major update since its creation 2014. The new edition is designed for all audiences, industry sectors and organisation types. 💡 The framework’s core is now organised around six key functions: 🔑 Identify🔑 Protect🔑 Detect🔑 Respond🔑 Recover🔑 Govern When considered together, these functions provide a […]
Browser extensions have become as common as mobile apps. People tend to download many and use few. There are over 176,000 browser extensions available on Google Chrome alone. These extensions offer users extra functionalities and customization options. While browser extensions enhance the browsing experience, they also pose a danger. Which can mean significant risks to […]
Cybersecurity has become paramount for businesses across the globe. As technology advances, so do the threats. Recognizing this, the U.S. Securities and Exchange Commission (SEC) has introduced new rules. They revolve around cybersecurity. These new requirements are set to significantly impact businesses. These rules are a response to the growing sophistication of cyber threats. As […]
You cannot overstate the importance of cybersecurity. Especially in an era dominated by digital advancements. Businesses and organizations are increasingly reliant on technology to drive operations. This makes them more susceptible to cyber threats. 66% of small businesses are concerned about cybersecurity risk. Forty-seven percent lack the understanding to protect themselves. This leaves them vulnerable […]
The topic of this post is the SPF, DKIM and DMARC authentication mechanisms and how we can utilise them to build a healthier mail exchange ecosystem. Contrary to popular belief, the role of SPF, DKIM and DMARC is not to protect a mail system against threats. That means they don’t work as an email security […]