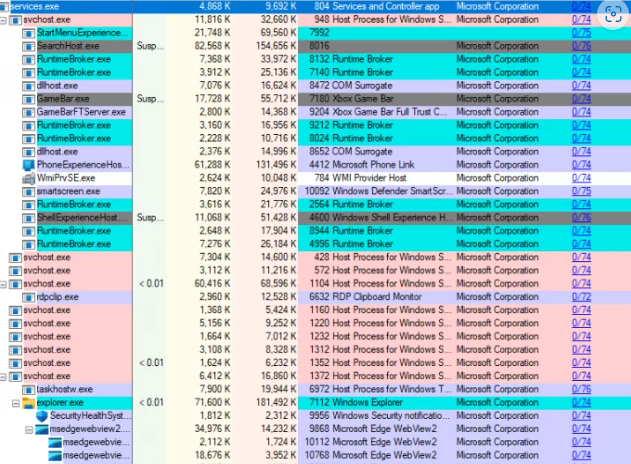
Sysinternals Process Explorer is a powerful tool for I.T professionals to monitor and manage system processes, security, and performance. The software, free to download from the Sysinternals website, was originally released in 1996 by Mark Russinovich and Bryce Cogswell and has since evolved to offer a comprehensive set of features for process management and system […]
🔍 What’s Happening? ⚠ Attackers overwhelm users with spam emails, primarily newsletter sign-up confirmations from legitimate organisations.⚠ Follow-up phone calls from individuals impersonating IT team members offer assistance and prompt users to download remote monitoring software like AnyDesk or use Microsoft’s Quick Assist feature.⚠ The goal is to establish a remote connection, allowing attackers to […]
Browser extensions have become as common as mobile apps. People tend to download many and use few. There are over 176,000 browser extensions available on Google Chrome alone. These extensions offer users extra functionalities and customization options. While browser extensions enhance the browsing experience, they also pose a danger. Which can mean significant risks to […]
The topic of this article is the Alternate Data Streams (ADS) feature, focusing on what it is and how and where it helps and discussing the sinister side of this NTFS File System feature. An Overview of Alternate Data Streams In the NTFS file system used in Microsoft Windows, every file comprises one or more […]
Cybercriminals can launch very sophisticated attacks. But it’s often lax cybersecurity practices that enable most breaches. This is especially true when it comes to small and mid-sized businesses (SMBs). Small business owners often don’t prioritize cybersecurity measures. They may be just fully focused on growing the company. They think they have a lower data breach […]
Remote work has become increasingly popular in recent times. It provides flexibility and convenience for employees. Additionally, telecommuting reduces office costs for employers. Many also cite productivity benefits due to fewer distractions. Research shows a 56% reduction in unproductive time when working at home vs. the office. But there are some drawbacks to working outside […]
In today’s digital landscape, cybersecurity threats continue to evolve. They pose significant risks to individuals and organizations alike. One such threat gaining prominence is zero-click malware. This insidious form of malware requires no user interaction. It can silently compromise devices and networks. One example of this type of attack happened due to a missed call. […]
This article refers to 6 steps to Effective Vulnerability Management for your Technology Technology vulnerabilities are an unfortunate side effect of innovation. When software companies push new updates, there are often weaknesses in the code. Hackers exploit these. Software makers then address the vulnerabilities with a security patch. The cycle continues with each new software […]