In today’s digital world, passwords are crucial in securing access to sensitive information. However, with the increasing number of online accounts and the complexity of password requirements, remembering, sharing and managing passwords poses a significant challenge for businesses. This is where Password Management software jumps in. The why’s Password Management software is a tool designed […]
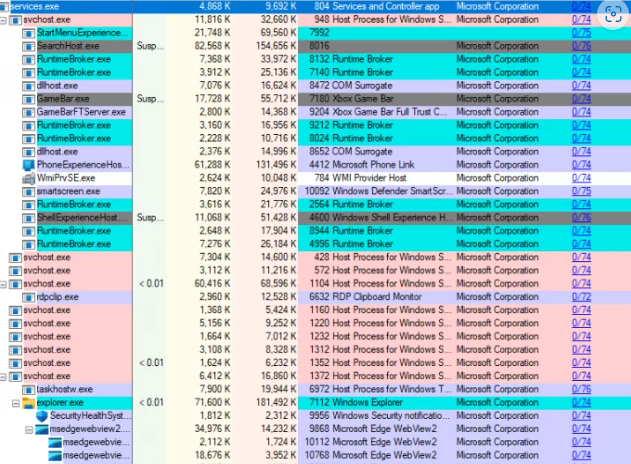
Sysinternals Process Explorer is a powerful tool for I.T professionals to monitor and manage system processes, security, and performance. The software, free to download from the Sysinternals website, was originally released in 1996 by Mark Russinovich and Bryce Cogswell and has since evolved to offer a comprehensive set of features for process management and system […]
💡 Our infographic highlights the key changes coming to Windows Server 2025, including new features and the removal of outdated functionalities. Here’s a quick rundown of what you need to know: New features:✅ A new functional level for forests and domains.✅ Delegated Managed Service Accounts (dMSA) with improved security.✅ Support for TLS 1.3 for LDAP […]
In an era where digital transformation is not just an option but a necessity, Microsoft 365 has emerged as the cornerstone of corporate productivity, enabling seamless communication, collaboration, and information management worldwide. However, the reliance on Microsoft 365 also introduces significant security vulnerabilities that can be exploited by cyber adversaries, making security vulnerability management an […]
📢 #NIST Releases Version 2.0 of Landmark Cybersecurity Framework. This is the first major update since its creation 2014. The new edition is designed for all audiences, industry sectors and organisation types. 💡 The framework’s core is now organised around six key functions: 🔑 Identify🔑 Protect🔑 Detect🔑 Respond🔑 Recover🔑 Govern When considered together, these functions provide a […]
Cybersecurity has become paramount for businesses across the globe. As technology advances, so do the threats. Recognizing this, the U.S. Securities and Exchange Commission (SEC) has introduced new rules. They revolve around cybersecurity. These new requirements are set to significantly impact businesses. These rules are a response to the growing sophistication of cyber threats. As […]
You cannot overstate the importance of cybersecurity. Especially in an era dominated by digital advancements. Businesses and organizations are increasingly reliant on technology to drive operations. This makes them more susceptible to cyber threats. 66% of small businesses are concerned about cybersecurity risk. Forty-seven percent lack the understanding to protect themselves. This leaves them vulnerable […]
The topic of this post is the SPF, DKIM and DMARC authentication mechanisms and how we can utilise them to build a healthier mail exchange ecosystem. Contrary to popular belief, the role of SPF, DKIM and DMARC is not to protect a mail system against threats. That means they don’t work as an email security […]
Introduction This blog post is about the critical topic of user security awareness training in businesses and organisations. Whether you’re a business owner or responsible for managing users within one, this article is for you. Cyber Security threats are on the rise, becoming more sophisticated daily. Malicious actors are looking for easy targets, and unfortunately, […]
The topic of this article is the Alternate Data Streams (ADS) feature, focusing on what it is and how and where it helps and discussing the sinister side of this NTFS File System feature. An Overview of Alternate Data Streams In the NTFS file system used in Microsoft Windows, every file comprises one or more […]
Software-as-a-Service (SaaS) has revolutionized the way businesses operate. It offers convenience, scalability, and efficiency. No more dragging software from one device to another. Everyone can collaborate easily in the cloud. But alongside its benefits, SaaS brings with it potential threats. When software and data are online, they’re more vulnerable to attacks. One of the latest […]
In today’s digital landscape, cybersecurity threats continue to evolve. They pose significant risks to individuals and organizations alike. One such threat gaining prominence is zero-click malware. This insidious form of malware requires no user interaction. It can silently compromise devices and networks. One example of this type of attack happened due to a missed call. […]
This article refers to 6 steps to Effective Vulnerability Management for your Technology Technology vulnerabilities are an unfortunate side effect of innovation. When software companies push new updates, there are often weaknesses in the code. Hackers exploit these. Software makers then address the vulnerabilities with a security patch. The cycle continues with each new software […]